We’ve known for several years that the U.S. internet is under insidious, perpetual and relentless attack by organized cybercrime all over the world. Now, here’s a new twist that is sure to snag many people … read this — be careful!
![]() We’ve known for several years that the U.S. internet is under insidious, perpetual and relentless attack by organized cybercrime all over the world, particularly China, Korea, Russia, Pakistan, Brazil, Nigeria; and even from within the U.S. Now we’ve seen a clever new scheme employed by these cyber criminals to compromise your computer and steal your identity. This new scheme began appearing in my mailbox over the last 36 hours. I received another half dozen in the mail this morning — all hoping I would fall for the realistic URLs (links) in the email. This is going to trap many, many people.
We’ve known for several years that the U.S. internet is under insidious, perpetual and relentless attack by organized cybercrime all over the world, particularly China, Korea, Russia, Pakistan, Brazil, Nigeria; and even from within the U.S. Now we’ve seen a clever new scheme employed by these cyber criminals to compromise your computer and steal your identity. This new scheme began appearing in my mailbox over the last 36 hours. I received another half dozen in the mail this morning — all hoping I would fall for the realistic URLs (links) in the email. This is going to trap many, many people.
The old rule “Never Click Unless you Know the Sender” has become unreliable. In these cases, the malware spam came from a “known” system and referred to “known” individual — ME! The new RULE is “Just Don’t Click” period — at least until you’ve validated where the link will take you. See important tips below.
The spammers and cyber criminals inform you that there’s a ‘problem’ in your mail server, and that you need to install a patch. They use your email address and your system, and even configure the domain links to look authentic. Many people will fall for this immediately because they do not know all of the users in their system. The User-groups.net system only has a few addresses, and all but one are spam honey pots.*
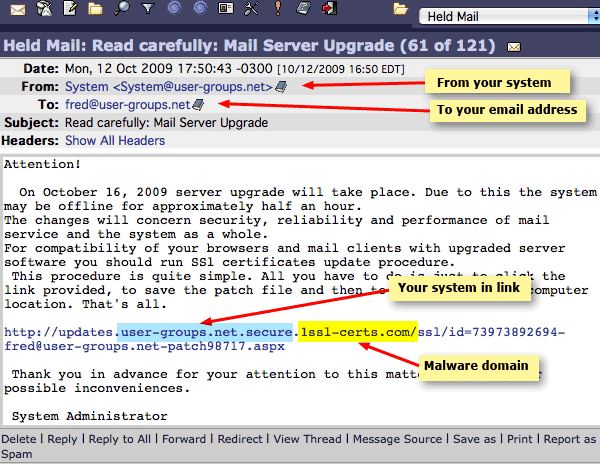
Notice that the criminal actually embedded our site’s URL and one of my email addresses into the link.
The domain name, 1SSL-CERTS.COM, actually has nothing to do with the UGN site, but is owned by someone who forged the Whois owner to be Irina V Sugakova in Morozova, Russia. The compromised server IP is actually at Hetzner Online AG in Gunzenhausen, Germany.
The results of the link would have attempted to load a botnet* malware*
onto my computer — and it may have been one of those bounty Trojan worms* I wrote about a couple of weeks ago in this article.
Today, these email entries appeared:
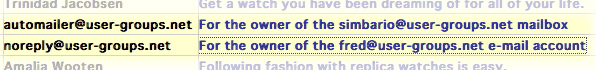
These guys are fine-tuning their scheme to include MY address, and more realistic domains.
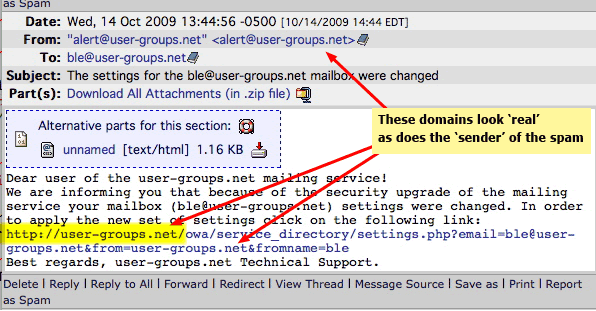
My first immediate tip-off is there has never been a “ble” user email address on UGN. While the link in the email looks totally authentic — giving me a brief startle — SpamCop’s special interface alerts me that there are embedded files and code in the email. So I went and selected “View Source”…
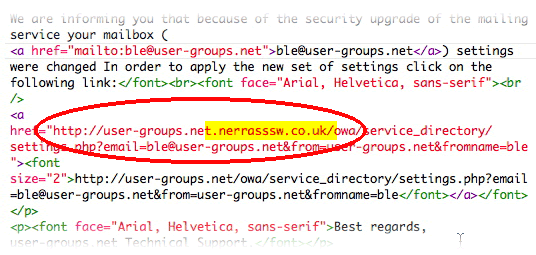
This time the criminal’s domain is Nerrasssw.co.uk, they set up “user-groups” as a sub domain. This domain was registered using a rogue registrar with a forged Whois* entry: Melissa Mohr, Fargo, Belgium. But the real IP address for the malware site is located in the Gansu province network of China Telecom, based in Beijing, China.
Several others today had totally different domains with different forged owners, but all had NS servers and IP addresses located on China Telecom.
Protect yourself from invasion

- Read suspicious mail starting with who it’s to and who it’s from
- Do not click any link until you’re sure where it goes
- Do not click images – their links cannot easily be seen
- Do not reply
- Delete the email, or forward to spam authorities
Link, domain, URL anatomy

The main element of the URL or “link” is the word-with-extension appearing just before the first slash in the URL, or domain.
Tip: go to the first single slash and back up. There will be a 1, 2, or 3 character extension, a dot, and the actual domain name. That’s where the link goes.
Many people subscribe to “disposable” email addresses, so they can switch once it becomes loaded with spam. The story above is another good reason to switch from gmail, yahoomail, or any other “disposable” address you may be using and invest in a SpamCop address. I use the account to keep the “Showker” pure — and all my other Showker addresses are all filtered through SpamCop, so I can report all the spam anyone attempts to send to any of my email addresses. Pure and simple, plus, I get to KEEP my email addresses I’ve had since the late 1980s.
Your email will be filtered by the most up to date spam rules in the industry and moved into a “held” folder. Then you can REPORT those spams, adding them to the global black list to protect email users all over the world. Thirty bucks a year is a very small price to pay for reliability and enforceability. Get your account at SpamCop.net.
Thanks for reading
Don’t forget … we encourage you to share your discoveries about favorite or famous graphic designers and illustrators with other readers. Just comment below, contact me here, or just give me a tweet at Twitter/DTG_Magazine
Further Reading:
- SpamCop Email System for Individuals
- Knujon Malicious Email News & Updates
- Report your spam, phishing and malicious emails to Knujon
- Learn the specific types of spam and junk email
- Boise State University: Anatomy of a URL
- Learn The Net dot com: Anatomy of a URL
- How to Report Spam at www.spamlaws.com
- The Federal Trade Commission Spam Page www.ftc.gov/spam/
- The U.S. Department of Justice Spam Page www.usdoj.gov/spam.htm